If you prefer to always view the website in English, please click here.
Phishing: what it is, how to spot it, and what to do if you are targeted by an impersonation attempt
Cybercriminals cast a wide net, fraudulently impersonating banks, insurance companies... and Endesa too. They want you to believe it is us so that you trust them and hand over sensitive data. Here is how to stop them.
In the digital age, almost all daily tasks are carried out by phone or via online channels: email, apps, websites, SMS, or messaging tools. Cybercriminals take advantage of any opportunity to steal personal data and use it fraudulently.
Direct, specialised attacks on company information systems are becoming increasingly frequent, as are individual attempts to manipulate customers and harvest personal information from the public digital world (internet and social networks). All with the sole purpose of obtaining personal data by impersonating a legitimate person or entity, such as your bank or energy supplier. This type of fraud is known as phishing.
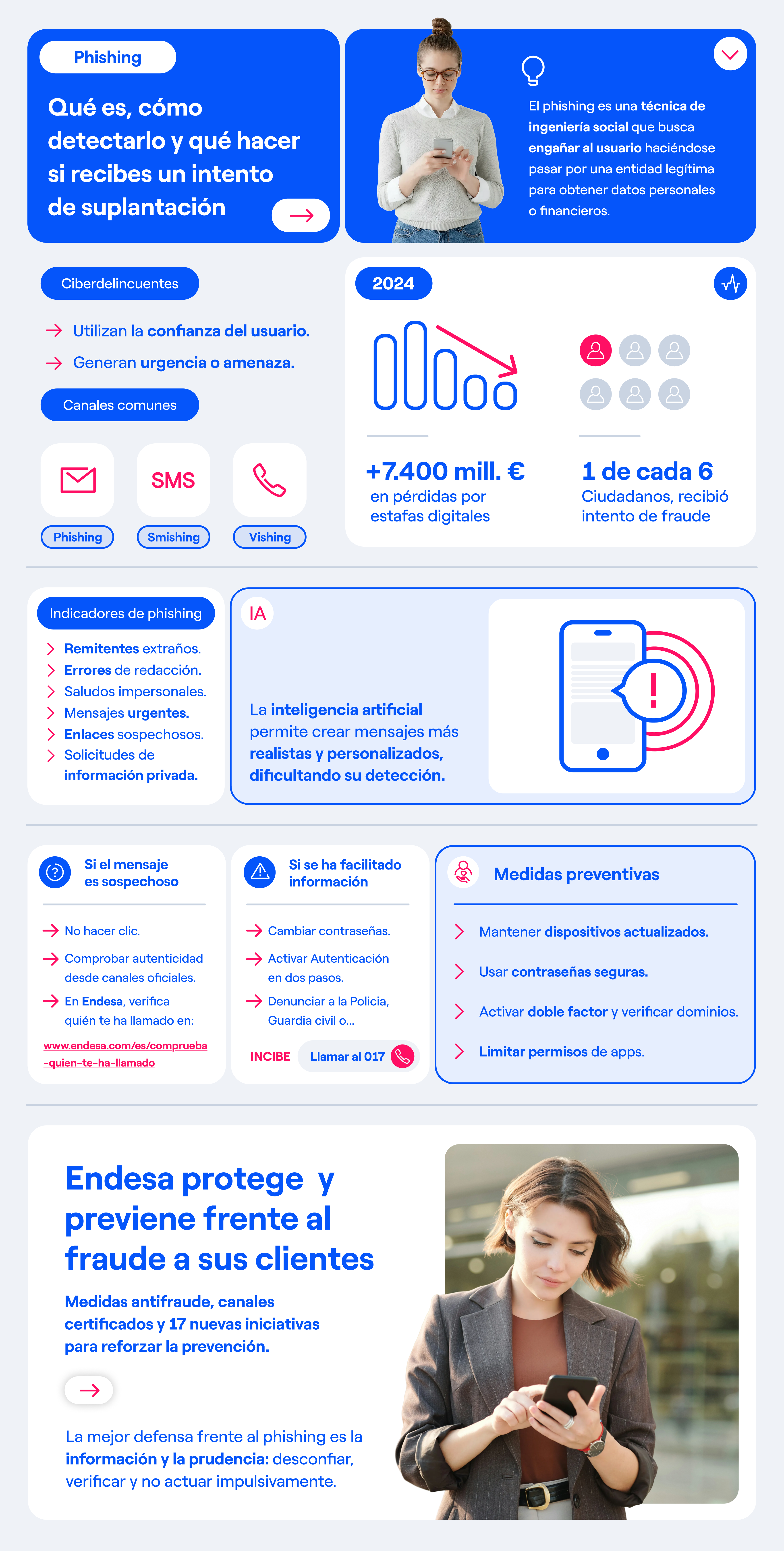
According to the Global Anti-Scam Alliance, digital scams caused losses of more than €7.4 billion in Spain in 2024, and one in six citizens was targeted by at least one fraud attempt.
Daily tasks with electricity suppliers, such as checking bills, signing up for contracts, or updating personal details, also carry risks if data is misused. Therefore, it is vital that you stay alert to identify phishing attempts and avoid falling for them.
What is phishing?
But when we talk about phishing specifically, what do we mean?
Phishing is a form of social engineering in which a cybercriminal or fraudster impersonates legitimate companies or institutions to persuade you to share sensitive information. There is a common pattern in this type of deception: exploiting your trust in a recognised person or entity by using personalised, friendly language, combined with a false sense of urgency or need.
The purpose of these fraudulent practices is to gain financial advantage or any undue advantage through the use or disclosure of sensitive or confidential information.
Most common forms of phishing
The term 'phishing' is over 30 years old, and the techniques used have evolved exponentially in the last three decades.
It is worth noting that the amount of money involved in cybercrime has been higher than the illegal drug trade for over five years. Cybercriminals dynamically adapt their tactics across different channels and media to target victims.
The most frequent phishing attacks use a mix of emails, SMS, and phone calls with friendly scripts and messages to manipulate customers—always with malicious intent. Credible stories, a friendly tone, highly personalised conversations, the use of technical data, pending bills, or contract updates are the most common hooks criminals use.
Email remains the most common channel. Attackers send a message that appears to come from a trusted entity with a subject line that generates alarm or urgency, such as a pending payment, a refund, or an account issue. The message usually includes a link redirecting to a fake page or an attachment that, when opened, installs malware on your device.
The evolution of cybercrime is directly linked to technological progress and the digitisation of society. In this context, artificial intelligence has made these attacks more sophisticated.
By accessing public information shared on social networks, cybercriminals generate highly personalised, realistic messages that are much harder to distinguish from the real thing. Furthermore, generative AI makes it increasingly easy to manipulate human emotions and behaviour.
Smishing (SMS phishing) is another widespread method. Here, an SMS arrives on your mobile with a link mimicking a company website. Its brevity and professional appearance increase the likelihood of you clicking the link.
Vishing (voice phishing) involves telephone fraud. The fraudster calls you directly and, using a convincing tone, requests personal or banking data, usually claiming they need to verify your identity, fix a system error, or threatening a penalty or service suspension.
Combining these channels (SMS, email, and phone) makes the story feel more real and increases the criminals' chances of success.
There are other specific types of phishing you should know about:
- Spear phishing
A targeted attack aimed at a specific individual or group within an organisation to gain access to sensitive information or compromise internal systems. These often look like emails from a colleague or manager requesting access to private documents or credentials.
- Whaling
A variant of spear phishing targeting senior executives or decision-makers to steal financial information, authorise transfers, or access sensitive data (e.g., fake emails supposedly from the CEO requesting an urgent transfer).
- Clone phishing
The attacker clones a legitimate email you previously received and resends it with a malicious link or attachment. The goal is to exploit your trust in the original message and trick you into giving away confidential information.
- Pharming
A technical manipulation that redirects you from a legitimate website to a fake one without you noticing, in order to steal passwords, credentials, or banking data (e.g., typing your bank's URL but being redirected to a fake replica designed to steal your login details).
Telltale signs of phishing
There are common indicators that help you recognise an impersonation attempt before it is too late:
- Suspicious sender: If the email address does not match the official one exactly, or uses strange domains, be suspicious.
- Unknown numbers: Stay alert to unexpected calls or messages. Verify the sender's identity before sharing any personal or sensitive data. Corroborate information by contacting the provider through their official channels.
- Spelling mistakes or use of unnatural language often betray translated scam texts.
- Impersonal/generic greetings ('Dear customer') or incorrect information.
- Urgency or threats: Messages demanding immediate actions or using threats ('your account will be blocked if you do not act immediately', 'we will proceed to suspend the service') if you don't respond instantly.
- Suspicious links: Never click a link unless you are certain the communication comes from an action you requested.
- Unusual requests: Be wary of companies requesting passwords, card numbers, or personal data via email or SMS. Be wary of requests to install data verification apps on personal devices and always go to official channels to verify authenticity.
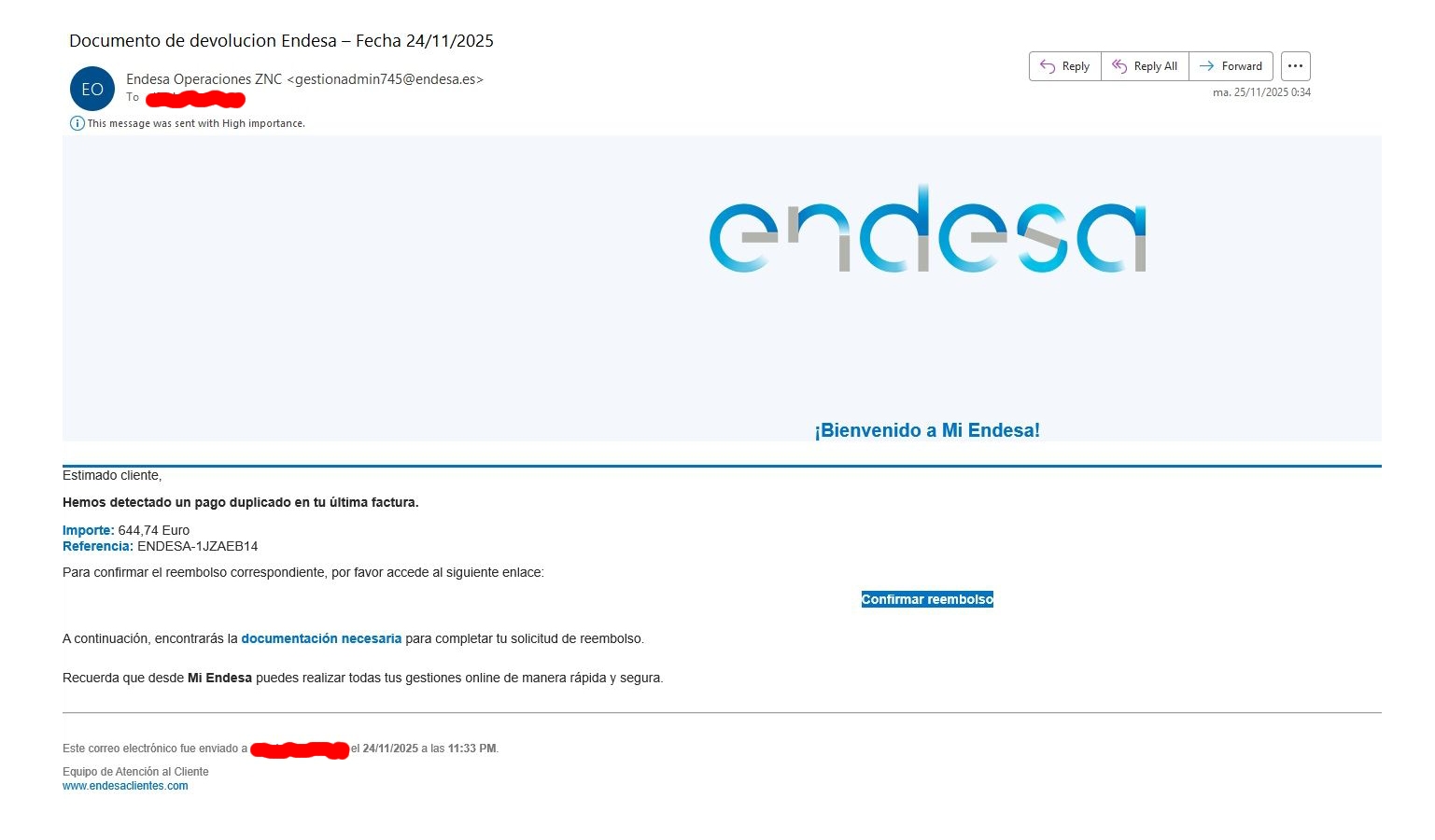
Examples of phishing using Endesa’s name
As the country's leading energy company, Endesa is a prime target for cybercriminals who try to use our reputation to trick victims. They have used orchestrated sophisticated phishing campaigns. For example, you might receive an email pretending to be from Endesa:
What to do if you are targeted by a phishing attempt
How you handle a cyberattack depends on the stage you are at. There are three main phases:
- Before a cyberattack.
- During the cyberattack attempt.
- Once you are aware that you have been the target of a scam.
Before a cyberattack: prevention
This phase is critical for preparing yourself as a potential target for cybercrime scams. No one is immune to phishing. You often unknowingly give away personal data, or your data may be obtained following a hack on third-party databases.
Regardless, you must stay informed, pay attention to relevant notices, and understand that fraudulent practices are more common than you might imagine.
Communication, information, and vigilance are your main allies. Generally, you should be somewhat suspicious and carefully scrutinise any advice or requests you receive. Don't get caught out by the unexpected.
Prevention is the most effective tool against phishing, so:
- Keep devices and software updated.
- Use unique, complex passwords and enable two-factor authentication (2FA) wherever possible.
- Verify website authenticity before entering personal data. Look for the padlock symbol and check the domain spelling.
- Limit app permissions and periodically review what access they have to your information.
Education and caution are essential. Understanding how digital scams work—and mistrusting messages that appeal to urgency, fear, or greed—can make the difference between spotting fraud and becoming a victim.
During the cyberattack attempt: caution
When you receive a suspicious message, the first rule is: do not interact with it. Activate your radar and act with caution. Do not click links or open attachments: One click can trigger malware or open a fake dialogue to steal your data.
Next, delete the message and contact the company via its official channels (phone, website, or app) to check if it was real.
At Endesa, we provide multichannel tools to help you verify communications. We recommend never clicking a link unless you are certain it relates to an action you requested.
Nationally, the Spanish National Cybersecurity Institute (INCIBE) offers free, confidential help by calling 017.
It is advisable to keep screenshots and details of the fraud attempt so authorities can investigate and prevent others from falling victim.
If the attempt comes via phone call: ask questions before engaging, clarify the purpose of the call, and never let yourself be pressured. Remember: you didn't initiate the call, so you need to understand the message fully. When in doubt, hang up and verify by calling the company's official number.
After an attack: speed
If you know you have been the victim of a cyberattack—for example, you provided sensitive info or downloaded a malicious file—time is decisive. You must act quickly.
Contact the relevant company (the service provider involved in the fraud to report the incident. This allows them to block suspicious operations and monitor irregular movements.
If you downloaded a file, run an updated antivirus scan and stop using the device.
If you supplied bank details (current accounts, IBAN, or credit card numbers), call your bank immediately to block charges and cancel cards.
Report the fraud. The main reporting channels in Spain are:
- The Spanish National Cybersecurity Institute (INCIBE), by calling the free number 017 or following the instructions on their website.
- The National Police, by visiting a station or using their online reporting form.
- The Civil Guard, via the Telematic Crimes Unit.
Reporting these facts not only protects the user but helps authorities identify fraud patterns and dismantle organised networks.
Finally, share your experience with your circle to help make fraud prevention a reality.
How we protect our customers and what we do about phishing attempts at Endesa
At Endesa, we apply security protocols that prevent the impersonation of our official channels and guarantee the authenticity of our communications. We never ask for personal information, passwords, or bank details via email or SMS.
Our official messages include verification systems such as digital signatures and certified domains, and corporate SMS come from verified numbers. We also provide a tool to verify if a call is legitimate.
When we detect fraud, we activate alert mechanisms and collaborate with authorities to neutralise the threat. We maintain a clear, direct, and dynamic strategy focused on protecting our customers and all their personal data.
Over the last year, we developed 17 communication and awareness initiatives aimed at customers, employees, and the general public. These actions include informative content, online campaigns, audiovisual materials, internal communications, and verification tools, all with one goal: to reinforce digital fraud prevention and raise the alert level against phishing attempts.
Caution is your best defence
Phishing is one of the most widespread digital threats, but also one of the most avoidable with the right information and tools.
Be suspicious of unexpected messages, always verify sources, and maintain good digital habits.
At Endesa, we reinforce our information systems every day to protect our customers, but total security against fraud requires collaboration between everyone: public bodies, companies, and customers.
In a world where technology moves exponentially, cybercrime is a constant threat. The best defence remains awareness and precaution.
Take a minute to find the product that best suits you:
{{firstStep.title}}
Take a minute to find the product that best suits you:
{{title}}
{{content.phone.title}}
{{content.phone.text}}
{{content.phone.phoneText}}
{{content.form.title}}
{{content.form.text}}
{{content.form.success.title}}
You don't need to adapt to Endesa's tariffs because they adapt to you. If you go to our catalogue you can compare the different tariffs for yourself. Or if you prefer, you can answer a few questions and we will take care of comparing all the different electricity and gas tariffs and then make a customised recommendation.
Take a minute to find the product that best suits you:
{{title}}
{{content.phone.title}}
{{content.phone.text}}
{{content.phone.phoneText}}
{{content.form.title}}
{{content.form.text}}
{{content.form.success.title}}
You don't need to adapt to Endesa's tariffs because they adapt to you. If you go to our catalogue you can compare the different tariffs for yourself. Or if you prefer, you can answer a few questions and we will take care of comparing all the different electricity and gas tariffs and then make a customised recommendation.
Comparison of Electricity and Gas Tariffs
You don't need to adapt to Endesa's tariffs because they adapt to you. If you go to our catalogue you can compare the different tariffs for yourself. Or if you prefer, you can answer a few questions and we will take care of comparing all the different electricity and gas tariffs and then make a customised recommendation.
Spend a minute to find the product which best adapts to you:
{{firstStep.title}}
Spend a minute to find the product which best adapts to you:
{{title}}
Spend a minute to find the product which best adapts to you: